You should take care about the values coming with the HTTP requests, because improper values are dangerous. These values can alter behavior of your application, generate runtime exceptions, and expose the error details to an attacker. You need to inspect these values and protect your application, by using a unified approach to sanitize them.
You can improve the security of your application, by performing data type consistency checkup. If you know that a parameter can contain only integer values, it’s a good practice to check that the passed value respects this requisite. Most primitive types (like System.Boolean, System.Integer, and System.DataTime) have a useful TryParse static method which checks that the corresponding value is convertible to a given type. If the conversion takes place, the value is saved in the variable and used in conjunction with the original value.
You can include the next code lines in your application to parse an Integer value from the query string.
Private Sub CheckID()Dim id As IntegerIf Integer.TryParse(Request.QueryString(“ID”), id) ThenEnd IfEnd Sub
The next picture shows the case if you do not test for a data type check. You can see that the default error page when the application is in debug mode also shows a fragment of the source code. Sometimes developers leave an application in debug mode even when it’s deployed:
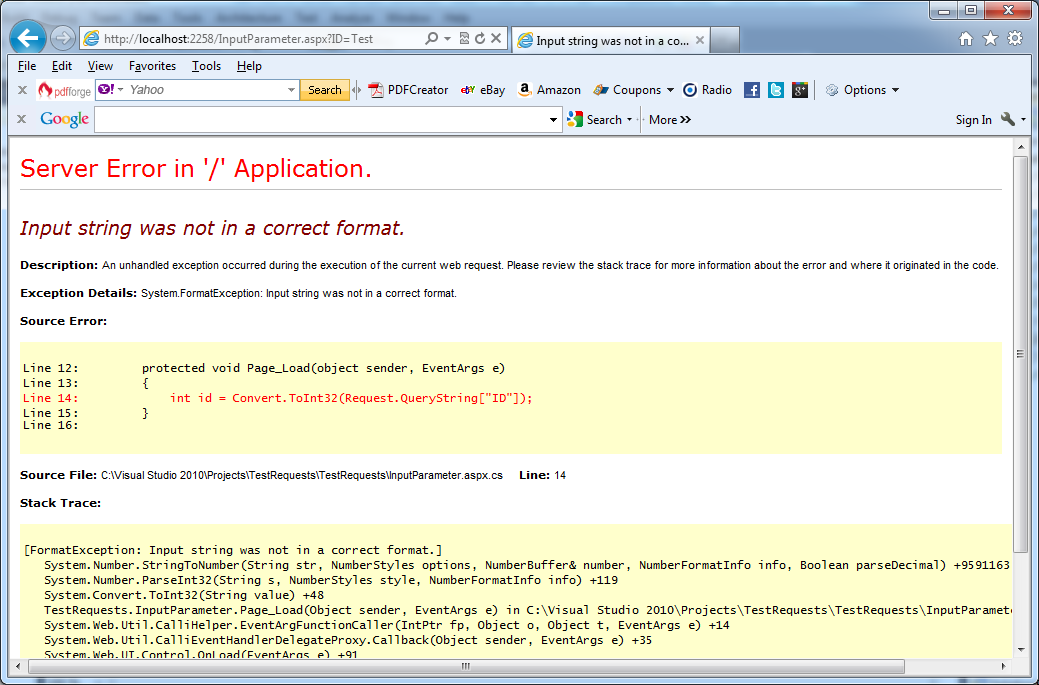
Disclosing of too many details about application if application’s parameters are not checked correctly in VB.NET
Important notes:
1. When you are dealing with the user input, you have to check for range consistency too.
2. Do not trust your user input and always verify that the values are within the acceptable range.
3. You can also add a blocking mechanism to your application, by implementing this technique proactively and logging unwanted requests.
